Introducing our Flagship Product, Athena MIS
the all-in-one management information system for independent training providers.
What is Athena?
Athena is an online management information system (MIS) that provides learner tracking, learner portfolio management and learning data management for independent training providers.
Who is Athena for?
Athena is a low-cost all-in-one MIS that helps independent training providers overcome compliance, evidence and data management challenges.
How do I know if Athena is for me?
Are you an independent training provider that…
- Manages training data with paper or Excel spreadsheets?
- Feels overwhelmed by compliance demands and deadlines?
- Is at risk of a poor Ofsted inspection report due to the mismanagement of data?
- Spends more time and resource on data management than you’d like?
- Currently pays for multiple data systems, or a high price for a market leading MIS?
Then Athena is for you.
How is Athena different?
- Our Standard 25 licence is 80% cheaper than the market leading MIS for independent training providers.
- Cheaper doesn’t mean cheap though. Athena matches and, in some cases, outsmarts the key features of other management information systems. It’s simply just better value for money.
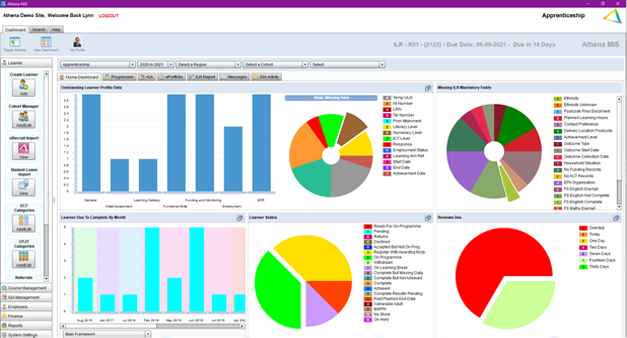
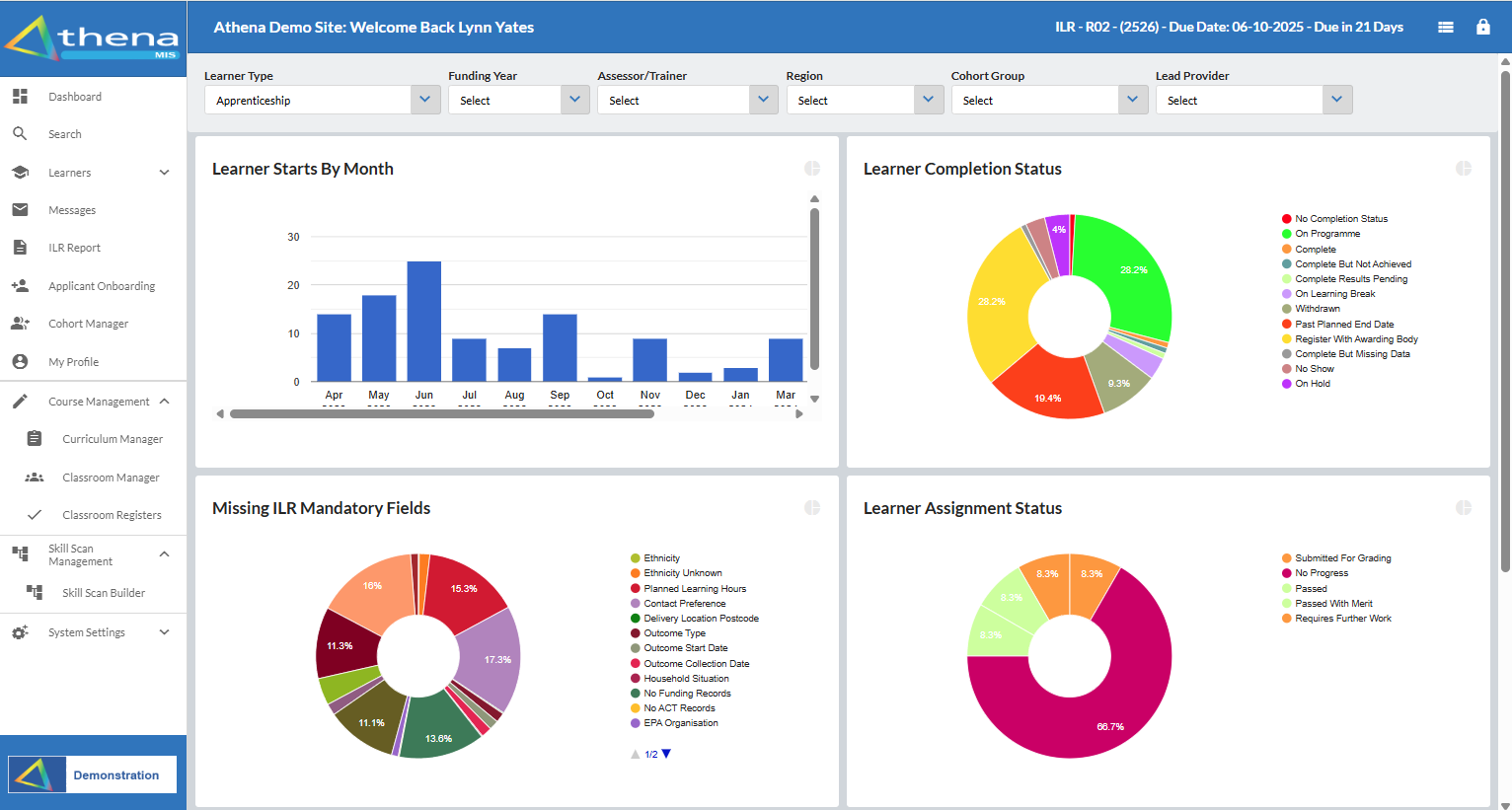
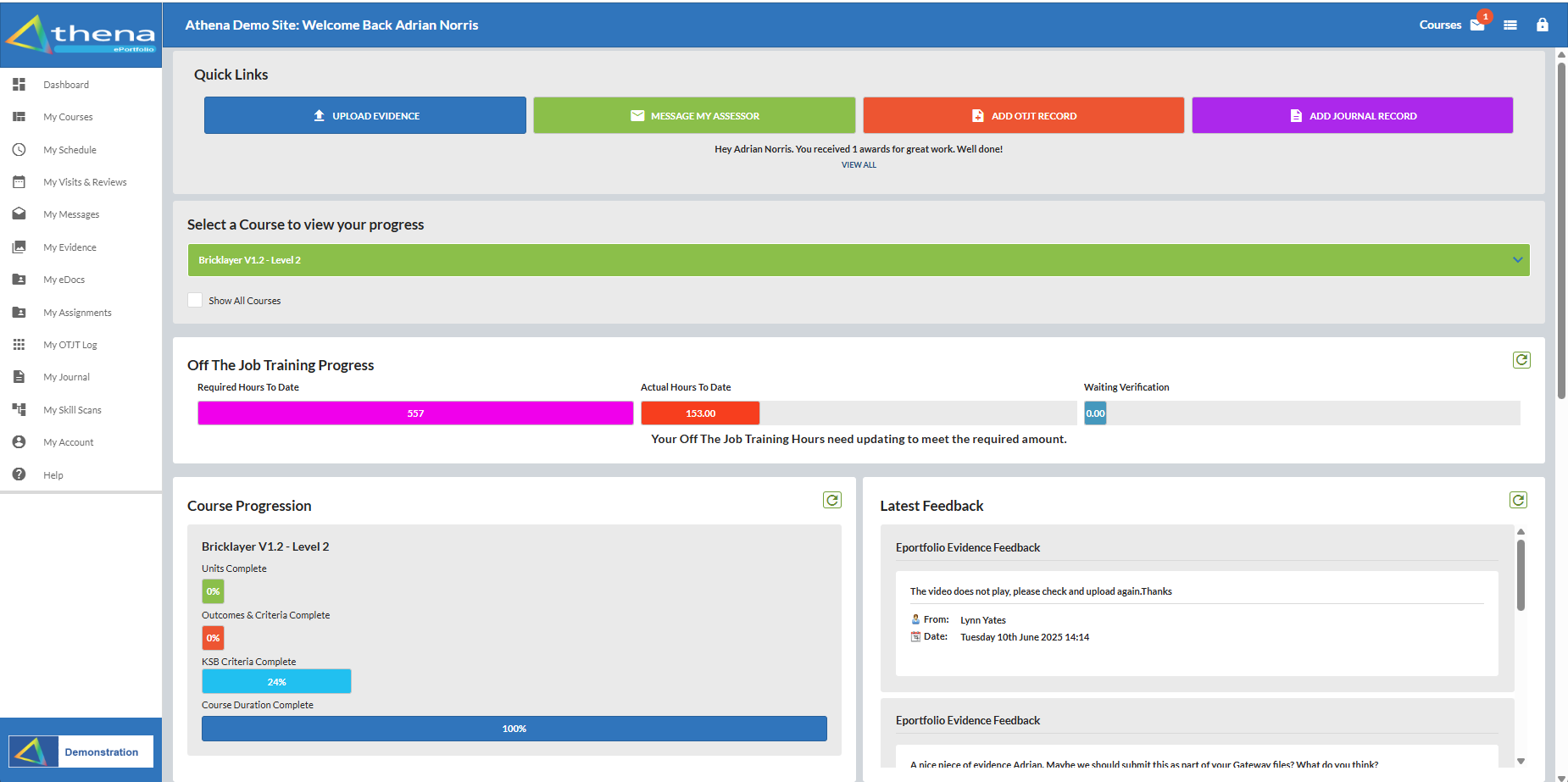
The Athena Key Features and Benefits

Compliance and Data Protection
We take great care of our data and as such follow the strict guidelines of Cyber Essentials Plus and IASME Governence amongst others.









